This entry will be about the technical perspective of the email server, while this topic may seem political it is not. I will disclose that I’m a Libertarian, and I did vote for Trump. However, that doesn’t sway my seasoned technical opinion because additionally I run an email server just like Hillary Clinton. The only bias within this should be the truth, and the considered possibility.
To understand, Email Service has not really evolved as the rest of the internet has. The internet was built on transparency, and open standards, security was an afterthought. Email Service Providers pioneered electronic mail as it was coined began in 1962. Lateron in the 1980’s POP mail became a standard for how email would transmit from the email server to the persons computer. Within the 1990’s a secure version of POP3S was instituted however not every email service made this their policy. In fact it had not become standard till after Edward Snowden made his debut about the NSA spying on everyone.
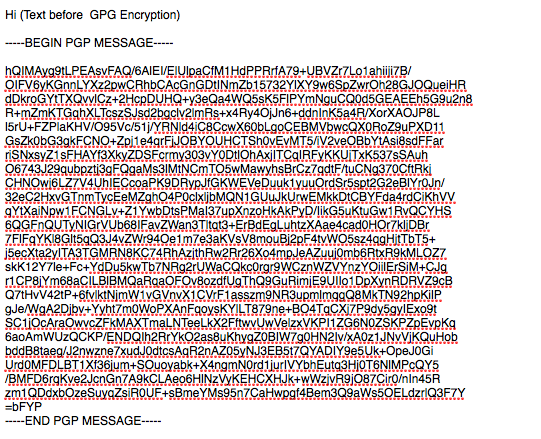
For the reader to understand all email sent and received from 1962-2013 was sent for anyone to see as if it was a postcard going through the post office box. With POP3S and IMAPS any email created as a draft on the Email Server was now encrypted, however the point in which an email was sent, the entire world can read it’s contents. The only email that is secure end to end is encrypting every email with PGP, or GPG which again is how Snowden, communicated to the Guardian before meeting. An example of this form of encryption is below.
Given, the example of this GPG text, ask yourself do you believe that Hillary, or her assistant(s) etc were using this as the primary means of communication, in addition to Obama, and other high ranking officials. This would be the first technical lie
As highlighted in this video
To understand and go point by point for the second video
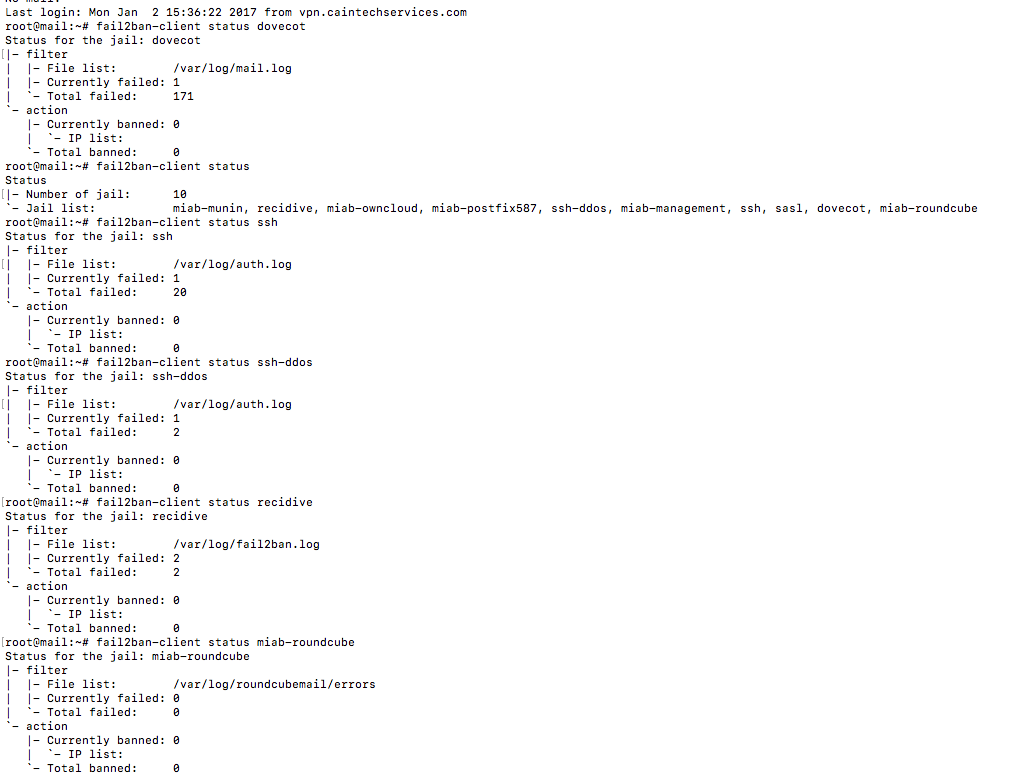
When, James Colmey is describing how email is transmitted regardless of what the email contained it went over a public internet in which nefarious actors could be laying in wait. The other is every server is routinely attacked, and in layman’s terms people jiggle the lock in order to try to get in. An example in a 7 hour period, there was 200 attack attempts on CainTech Services Email server. These were failed, and banned attempts to a unknown email service to the planet. Can one imagine the amount of attempts for a governmental official?
 .
.
Above, is a log by Fail2ban which acts like a night watch guard banning and blocking bad attempts and preventing future attacks. The failure rate in which it is banned is one wrong attempt. The second attempt is a 20 year ban from the server, unless the server administrator whitelists, and unblocks the blacklisted IP address. This is a practice that I administer which is a strict policy.
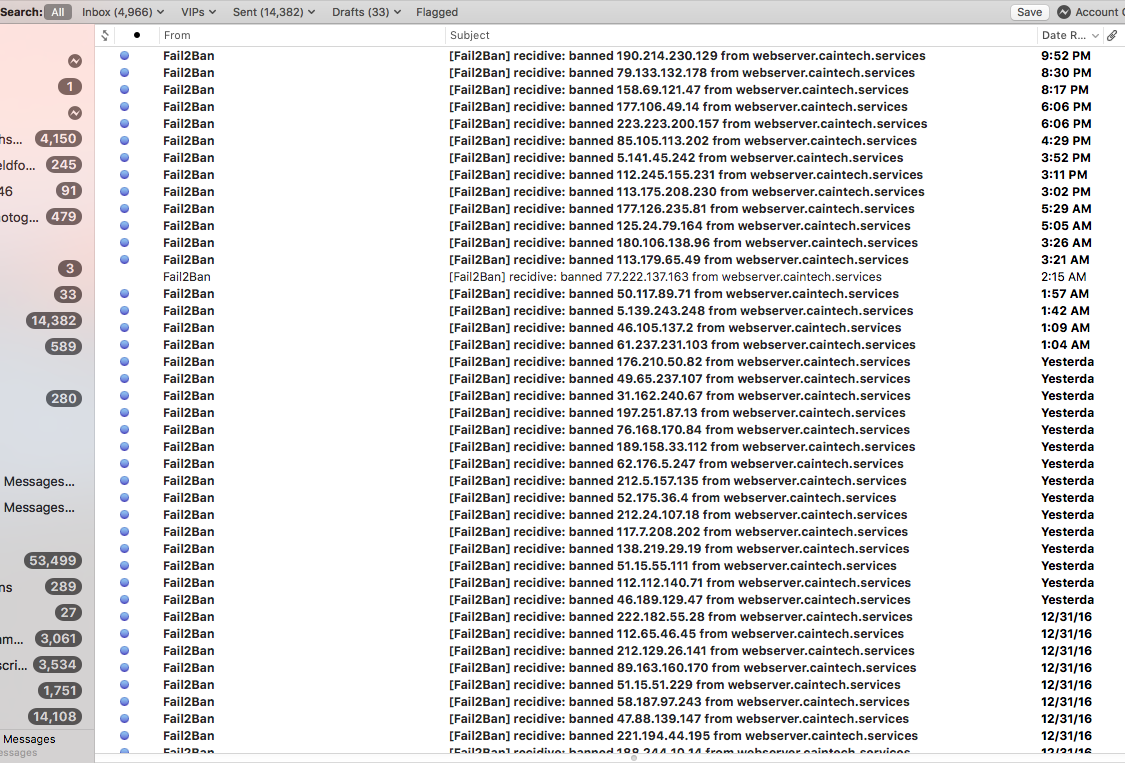
Secondly, in one month, my webserver was probed 4,996 times for bad wordpress login attempts, or other methods of entry. My webserver hosts a hundred domain(s) with 1-3 users per website. In 2016, I instituted encryption, on the webserver, and all websites against the logins of all websites that had Wordpress, or other CMS style websites. Even, though it maybe overkill an SSL certificate validates for any client, or user that they are visiting a secure and legitimate website in whom they intend to visit. This practice is used on the Email Server, as well. In today’s world Below is a screenshot of emailed ban attempts from the webserver.
In terms of Governmental standards for encryptions, whether it’s ciphers, or SSL Certificates, there are four important compliance measures HIPAA, FIPS, NIST, and PCI DSS To note each of these compliance measures incorporate ciphers has different levels of enforced security. Federal Information Processing Standard (FIPS) includes old vulnerable ciphers of encryption, that are vulerable to known attacks. Could this alone explain, Hillary’s server being hacked. HIPAA guidelines are additionally out of date, these may have been superior standards at one time. Though have seen been proven weak. National Institute Of Standards And Technology (NIST) also requires weak ciphers as of 2015. In short the private sector/open source ciphers are known to be the strongest ciphers, because there is no known vulnerability. These ciphers can become weak over time.
Again to note even if Hillary meant well in a professional IT experience the odds are in favor that her server was hacked, and compromised only due to the fact she attracts international attention. While using a server inside her residence. Secondly, the fact that she sent unencrypted email across the internet which in itself would attract attention. Third the Federal Guidelines for securing communications are out of date so much so the standard FIPS ciphers are 15 years out of date. NIST is out of date by one year and HIPAA as well. Fourth is people whom she was in contact with her hacked, which means she was the primary target. The only explanation is that Hillary, either was relaxed about security matters, or hired incompetent staff and IT personnel.